- docker rm $(docker ps -a -q)
- docker rmi $(docker images -q)
Virtualization
- Docker 모든 이미지 및 컨테이너 삭제 2019.07.28
- ESXi 6.7에 Photon OS 3.0을 설치 후 기본설정 2019.07.28
- VMware Fusion FDD 추가시 사용 이미지 2018.03.09
- esxi update (zip 파일 이용 수동) 2018.01.11
- Vmware Esxi Update No Space Left On Device Error 조치, esxi patch (zip 형태 패치) 다운로드 2018.01.11
- VMware ESXi 및 워크스테이션 인텔 CPU 취약점 보안 패치(meltdown 보안패치) 2018.01.05
- esxi 6.5 virtual fdd image 생성(가상 플로피 디스켓 파일 생성) 2017.12.09
- ESXi 6.5 Update (업데이트) 2017.12.06
Docker 모든 이미지 및 컨테이너 삭제
ESXi 6.7에 Photon OS 3.0을 설치 후 기본설정
호스트 OS위에 많은 도커 컨테이너가 돌아가면 하드웨어 효율성을 극대화할 수 있지만
단점으로 호스트 OS의 보안취약성을 이용해 해커가 뚫으면 컨테이너가 위험에 노출되고
호스트 OS가 다운되면 전체 컨테이너 서비스 장애가 발생할 수 있겠습니다.
VMWare 사에서 Docker 컨테이너 운영에 최적화된 OS를 만들었는데 벌써 버전 3.0이 되었나 봅니다.
이 OS를 ESXi 하이퍼바이저에 설치 후 Docker 컨테이너를 운영하되 photonos를 여러개 설치해서 컨테이너를 분산시키면 처음 말한 보안 및 안정성 이슈를 완화하는 효과가 나타나겠습니다.
(photonos 외에 컨테이너에 최적화된 여러 os가 있습니다.)
https://vmware.github.io/photon/
- Optimized for VMware vSphere®: The Linux kernel is tuned for performance when Photon OS runs on vSphere.
- Support for containers: Photon OS includes the Docker daemon and works with container orchestration frameworks, such as Mesos and Kubernetes.
- Efficient lifecycle management: Photon OS is easy to manage, patch, and update.
- Security hardened: The kernel and other aspects of the operating system are built with an emphasis on security.
다음은 ESXi 6.7에 단순히 photonos 3.0을 설치하고 기본 설정을 하는 방법입니다.
1. ESXi 6.7에 설치하기
photonos 사이트에서 OVA 배포 파일을 다운로드 (OVA with virtual hardware v13 (UEFI Secure Boot)) 한 후
ESXi 6.7에서 OVA Import 하면 끝입니다! 용량은 153M 정도입니다.
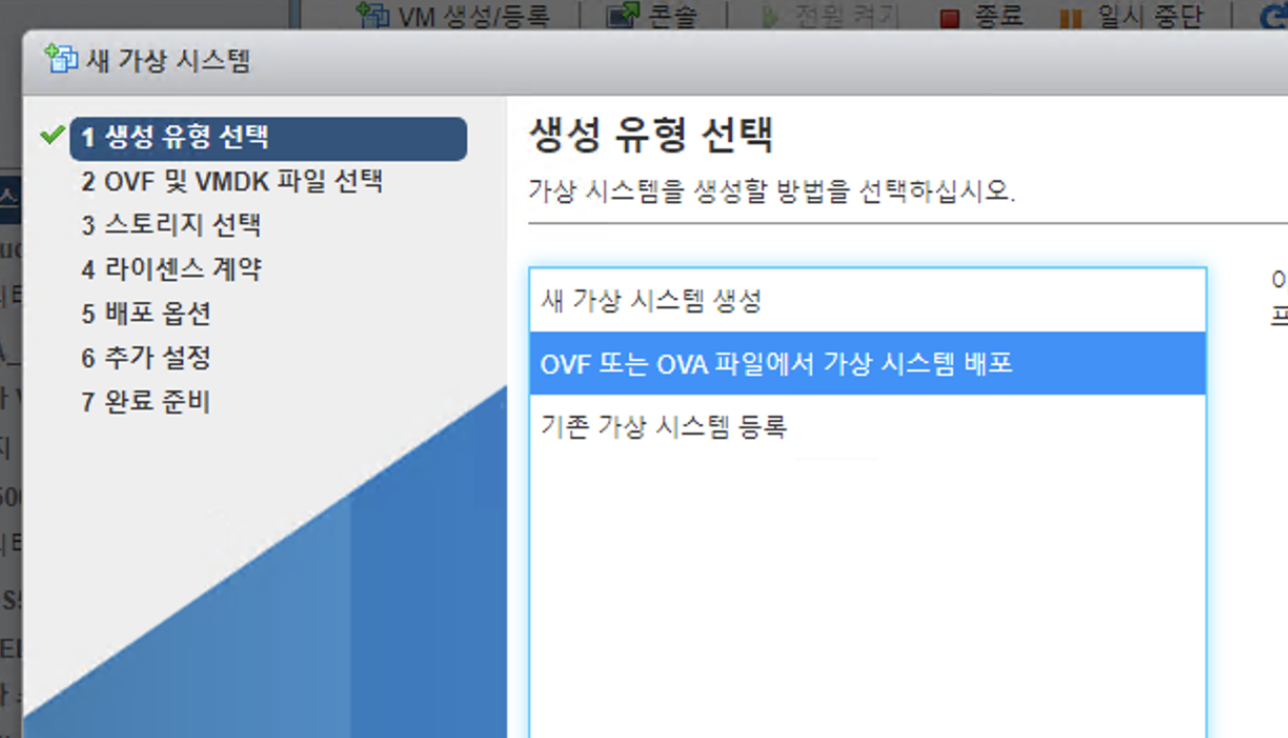
2. PhotonOS 기본설정
2-1. 초기 로그인 ID : root , 초기 로그인 PW : changeme
2-2. IP 보기 : ip a
2-3. IP 변경 :
cd /etc/systemd/network
mv 99-dhcp-en.network 10-static-en.network
chmod 644 10-static-en.network[Match]
Name=eth0
[Network]
Address=198.51.0.2/24
Gateway=198.51.0.1systemctl restart systemd-networkdhttps://vmware.github.io/photon/assets/files/html/3.0/photon_admin/setting-a-static-ip-address.html
2-4. Root로 SSH 로그인 허용 (PermitRootLogin yes)
vim /etc/ssh/sshd_config
# override default of no subsystems
Subsystem sftp /usr/libexec/sftp-server
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
PermitRootLogin yes
UsePAM yessystemctl restart sshd2-5. Docker 활성화
systemctl status docker
systemctl enable docker
systemctl start docker
2-6 업데이트
tdnf update
유용한 링크들
https://medium.com/@darkrasid/docker%EC%99%80-vm-d95d60e56fdd
http://egloos.zum.com/mcchae/v/11314059
VMware Fusion FDD 추가시 사용 이미지
맥 터미널에서 빈 flp 파일을 생성하면 됩니다. 터미널에서 다음 명령어를 이용해주세요.
touch floppy144.flp
다른 방법 및 자세한 내용은 아래를 참고해주세요.
아래
Solution
- Insert the floppy that you want to image.
- Open the Disk Utility in the Utilities folder.
- Select the floppy disk and click New Image.
- Rename the image if you want to.
- Ensure that the image format is set to Read/Write.
- Click Save.
- When the image is complete, replace the floppy image file extension of dmg with flp so it is recognized by VMware Fusion.
- Click on the desktop, then from the top menu bar, click File > New Finder Window
- In the finder window, click on Applications > Utilities > Terminal.
- At the command prompt, run:
touch floppy144.flp - Configure the virtual machine to use the file floppy144.flp as a floppy disk image.
- Within the guest operating system, format the attached floppy disk (image) and use normally.
출처 : https://kb.vmware.com/s/article/1002195
esxi update (zip 파일 이용 수동)
다운로드 받은 zip 파일을 데이터 스토어에 올리고 메인터넌스 모드에서 아래 명령어를 참고해서 ssh에서 실행 후 재부팅 하면 됩니다.
no space 에러가 발생하면 http://vhrms.tistory.com/792?category=575946 를 참고해 보세요.
esxcli software profile update -d /vmfs/volumes/SSD/esxi\ sp/ESXi650-201712001.zip -p ESXi-6.5.0-20171204001-standard
주의할 부분은 패치 경로와 파일명, 그리고 -p 옵션뒤에 오는 프로파일 명입니다. 프로파일 명은 vmware공식 홈페이지에서 확인할 수 있습니다.
it gives that error:
[InstallationError]
[Errno 28] No space left on device
위와 같은 에러가 나오면서 ESXi 업데이트 설치가 안된다면 아래 링크를 참고해서 swap 공간을 설정해주세요.
https://knowledgegainedandshared.com/2017/04/17/how-to-setup-swap-in-esxi-6-5/
esxi patch (zip 형태 패치) 다운로드
https://my.vmware.com/group/vmware/patch#search
VMware ESXi 및 워크스테이션 인텔 CPU 취약점 보안 패치(meltdown 보안패치)
패치 적용 방법 :
# Cut and paste these commands into an ESXi shell to update your host with this Imageprofile # See the Help page for more instructions # esxcli network firewall ruleset set -e true -r httpClient esxcli software profile update -p ESXi-6.5.0-20180104001-standard \ -d https://hostupdate.vmware.com/software/VUM/PRODUCTION/main/vmw-depot-index.xml esxcli network firewall ruleset set -e false -r httpClient # # Reboot to complete the upgrade
2018-01-09
Imageprofile ESXi-6.5.0-20180104001-standard (Build 7526125) includes the following updated VIBs:
| Name | Version | Vendor | Summary | Category | Severity | Bulletin |
|---|---|---|---|---|---|---|
| cpu-microcode | 6.5.0-1.38.7526125 | VMware | Updates the ESX 6.5.0 cpu-microcode | bugfix | important | ESXi650-201801402-BG |
| esx-base | 6.5.0-1.38.7526125 | VMware | Updates the ESX 6.5.0 esx-base | bugfix | important | ESXi650-201801401-BG |
| esx-tboot | 6.5.0-1.38.7526125 | VMware | Updates the ESX 6.5.0 esx-tboot | bugfix | important | ESXi650-201801401-BG |
| vsan | 6.5.0-1.38.7395176 | VMware | Updates the ESX 6.5.0 vsan | bugfix | critical | ESXi650-201801401-BG |
| vsanhealth | 6.5.0-1.38.7395177 | VMware | ESXi VSAN Health Service | unknown | unknown | ESXi650-201801401-BG |
(For more information see KB52200.)
출처 : https://esxi-patches.v-front.de/ESXi-6.5.0.html
1. Summary
VMware ESXi, Workstation and Fusion updates address side-channel analysis due to speculative execution.
2. Relevant Products
- VMware vSphere ESXi (ESXi)
- VMware Workstation Pro / Player (Workstation)
- VMware Fusion Pro / Fusion (Fusion)
3. Problem Description
Bounds-Check bypass and Branch Target Injection issues
CPU data cache timing can be abused to efficiently leak information out of mis-speculated CPU execution, leading to (at worst) arbitrary virtual memory read vulnerabilities across local security boundaries in various contexts. (Speculative execution is an automatic and inherent CPU performance optimization used in all modern processors.) ESXi, Workstation and Fusion are vulnerable to Bounds Check Bypass and Branch Target Injection issues resulting from this vulnerability.
Result of exploitation may allow for information disclosure from one Virtual Machine to another Virtual Machine that is running on the same host. The remediation listed in the table below is for the known variants of the Bounds Check Bypass and Branch Target Injection issues.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifiers CVE-2017-5753 (Bounds Check bypass) and CVE-2017-5715 (Branch Target Injection) to these issues.
Column 5 of the following table lists the action required to remediate the observed vulnerability in each release, if a solution is available.
VMware Product
Product Version
Running on
Severity
Replace with/ Apply Patch
Mitigation/ Workaround
* This patch has remediation against CVE-2017-5715 but not against CVE-2017-5753.
4. Solution
Please review the patch/release notes for your product and version and verify the checksum of your downloaded file.
VMware ESXi 6.5
Downloads:
https://my.vmware.com/group/vmware/patch
Documentation:
http://kb.vmware.com/kb/2151099
VMware ESXi 6.0
Downloads:
https://my.vmware.com/group/vmware/patch
Documentation:
http://kb.vmware.com/kb/2151132
VMware ESXi 5.5
Downloads:
https://my.vmware.com/group/vmware/patch
Documentation:
http://kb.vmware.com/kb/2150876
VMware Workstation Pro, Player 12.5.8
Downloads and Documentation:
https://www.vmware.com/go/downloadworkstation
https://www.vmware.com/support/pubs/ws_pubs.html
VMware Fusion Pro / Fusion 12.5.9
Downloads and Documentation:
https://www.vmware.com/go/downloadfusion
https://www.vmware.com/support/pubs/fusion_pubs.html
esxi 6.5 virtual fdd image 생성(가상 플로피 디스켓 파일 생성)
윈도우에 Winimage 체험판 프로그램을 설치 후 실행
1. File -> New -> 1.44MB -> (플로피디스크에 담을 파일이 있다면 추가) OK -> 디스켓 저장버튼 클릭하여 vfd, flp 형식으로 저장
2. esxi 웹콘솔에서 가상 머신 편집 후 플로피디스크 하드웨어 추가 후 좀전에 만들 이미지를 데이터스토어에 업로드한 후 열기 하면 되었습니다.
출처 : https://pricklytech.wordpress.com/2011/07/10/how-to-create-a-virtual-floppy-for-vmware-vsphere/
ESXi 6.5 Update (업데이트)
https://esxi-patches.v-front.de/ESXi-6.5.0.html
위 주소로 이동하면 업데이트 하는 방법이 설명되어져 있습니다.
글 작성일 기준으로 아래의 방법으로 하면 Build 6765664 버전으로 업데이트 됩니다.
2017-10-05
Imageprofile ESXi-6.5.0-20171004001-standard (Build 6765664) includes the following updated VIBs:
Name Version Vendor Summary Category Severity Bulletin
esx-base 6.5.0-1.29.6765664 VMware Updates the ESX 6.5.0 esx-base bugfix critical ESXi650-201710401-BG
esx-tboot 6.5.0-1.29.6765664 VMware Updates the ESX 6.5.0 esx-tboot bugfix critical ESXi650-201710401-BG
vsan 6.5.0-1.29.6765666 VMware Updates the ESX 6.5.0 vsan bugfix critical ESXi650-201710401-BG
vsanhealth 6.5.0-1.29.6765667 VMware ESXi VSAN Health Service unknown unknown ESXi650-201710401-BG
(For more information see KB2151082.)
# Cut and paste these commands into an ESXi shell to update your host with this Imageprofile
# See the Help page for more instructions
#
esxcli network firewall ruleset set -e true -r httpClient
esxcli software profile update -p ESXi-6.5.0-20171004001-standard \
-d https://hostupdate.vmware.com/software/VUM/PRODUCTION/main/vmw-depot-index.xml
esxcli network firewall ruleset set -e false -r httpClient
#
# Reboot to complete the upgrade

